Pronounced like "fishing", phishing is a technique used by those with malicious intent to trick you into providing sensitive information online, like username/passwords, credit card payments information, and bank account information. This is obviously important for you to be aware of as an individual, but even more so as a business owner.
People who engage in phishing techniques vary in skill. The idea is they masquerade themselves as a known and trusted business, send you an email that appears to come from that business, and then ask you to click on a link in the email to confirm or enter information. Some phishing attempts are obvious, with blatant typos in the phishing email, shabby graphics, and suspect English. Others are highly skilled ... and even the most savvy internet user can be "taken" by the deceptive phishing attempt.

Phishing attempts used to be limited to email for the most part, but now you'll find phishing attempts across social media channels, including Facebook, Twitter, Google+ and LinkedIn. Some of the phishing attempts you may have seen in recent years appear to come from well known banks and the IRS. If you've ever been manipulated by a phishing scheme, you know the stress and trauma it can cause, not to mention the potential financial issues that can arise.
As a business owner who accepts online credit card payments, it's important to understand what phishing is. The worse case scenario is a malicious attempt to masquerade as YOUR business and solicit your customers for personal information. Business system security is the first step in protecting your business against this activity, but understanding what phishing criminals do to try to manipulate you and your customers is also essential. Information is power.
Types of Phishing
Phishing
As we've already defined it, phishing is a simple attempt to collect sensitive information using a disguised electronic communication.
Spear Phishing
This is a more targeted phishing attempt in which the perpetrator gains personal information about the target before sending the phishing attempt. Personalizing the communication makes it more effective.
Clone Phishing
Clone phishing is when a perpetrator takes an ACTUAL email that was sent from a trusted source, copies it, and then resends it. These are highly effective for phishers, as well.
Whaling
Whaling is a phishing attempt targed at high level executives or high profile individuals.
Rogue WiFi
This phishing technique is slightly different in that the perpetrators setup rogue free WiFi hot spots rather sending electronic correspondence. They configure them to run man-in-the-middle (MitM) attacks to steal sensitive information.
Phishing Techniques
Link Manipulation
By far the most common technique used is link manipulation. An individual will receive an email that appears to come from a trusted source (i.e. their bank) asking them to click on a link to verify information. Often, there is a scare tactic used. For example, "your account may have been compromised ... click here to reset your password".
The example below is a low quality phishing attempt, but rest assured, there were likely thousands of people who fell for it.
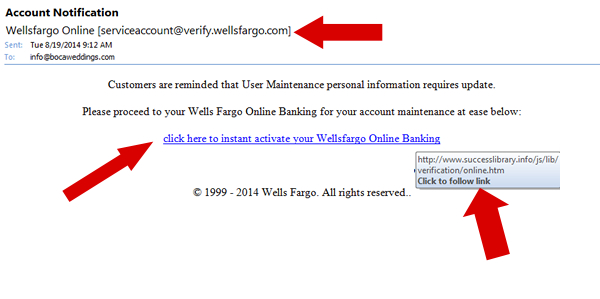
Notice the email appears to be from Wells Fargo. However "Wells Fargo" is misspelled as "Wellsfargo". The email address it's from appears to be legit as serviceaccount@verify.wellsfargo.com. In this case, the quality of the writing in the email is suspect, but it provides a link for the recipient to click to update their account information. Many people will simply click the link and do what is asked of them ... this is a mistake. When you roll your cursor over the link, you can see that the link does NOT take the user to Wells Fargo. Instead, it takes the user to a website called "www.successlibrary.info". This is definite evidence of a phishing scheme. Once on this "suspect" website, the user may be asked to enter login information ... OR the website may just automatically download a trojan virus or keystroke tracking malware to the user's computer.
There are several other phishing techniques out there including filter evasion, website forgery, phone phishing, and tab nabbing. However, by far the most common technique involves link manipulation in emails that come from what appear to be trusted sources.
Protect Your Business & Your Customers
As a business owner who accepts online credit card payments and debit card payments, and who may have login areas for customer access, it's important for you to understand that there are criminals out there who attempt to take advantage of businesses to gain access to customer card holder data and bank account information.
You should educate your customers about never clicking on links in emails. As a customer, they should ALWAYS go directly to your website by entering the URL in their browser window before entering any type of payment information, login information, or personal information of any kind.
It's also critical that you keep your business systems secure so your client lists and their contact information cannot be compromised. If a perpetrator gains access to your client list they can engage in spear phishing ... it empowers them with information that enables them to personalize phishing emails to your customers, making it more likely that your customers will click through to the nepharious link.
Who is Novera Payment Solutions?
Novera Payment Solutions is well known as a leader in the credit card payments industry and is committed to helping businesses improve their bottom line by providing significant savings on credit card processing fees through our innovative flat fee merchant account.
Contact Novera to learn more about how we work with small businesses to provide the most fair and transparent pricing structure available on the market today for credit card processing and debit card processing.